As Helical Insight supports Multi-tenancy, users would like to see data which is relevant to them. For example, Sales managers would like to see the reports/dashboards of sales data, Finance managers would see only financial reports etc.
For that, ‘Metadata security’ feature can be used in which user can grant or deny the permission of viewing tables/columns to particular users/roles/profiles. Note that this data security feature can only be applied through ‘Metadata’.
Following are the steps to apply data security:
Step 1: Select the ‘Security’ tab whilst creating/editing a metadata

Step 2: Select the table/column/view on which the security is to be applied from the panel present at the left.

Step 3: Enter the Expression name for the data security for further reference
Step 4: The column/table/view that you select for applying the data security will appear in the ‘Entity name’ field. Users can select multiple tables/views/columns at one time by clicking on ‘add more’

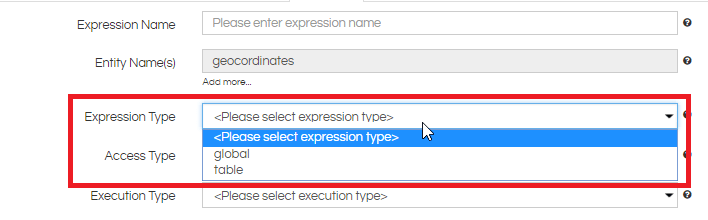
Step 5: Select the Expression type. It can be table, column or global. Global expression can be used when complete metadata is to be applied data security.
Note that users would be able to see global expression only when they select a table.
Step 6: Select the access type, which is either grant or deny

Grant permission: If a grant access to tables/Views/columns is selected for a particular set of user/users, then only those users would be able to view the reports. That means users other than those selected while applying the security would not be able to access the tables/Views/columns.
Deny permission: Selected users/roles/profile would not be able to access the selected tables/Views/columns.
Use case: Let’s say there are 100 users in an organisation. You want only 2 of them to access the ‘Revenue’ column in the metadata. It would not be feasible to provide ‘deny’ permission to these 98 users for 98 times. Better way would be to provide ‘grant’ permission to the remaining 2 users.
Step 7: Select the execution type either from ‘condition if’ or ‘groovy’

ConditionIf: When execution type is condition if, the application expects the condition to be a simple expression that can be evaluated to be true/false by Spring Expression Language (SpEL). Using SpEL users can write various simple as well as complex expressions that will be evaluated on runtime to restrict metadata/data for query generation.
When conditionIf is given for filter expression, the application expects conditionIf to return a string that will be applied to the report created using the metadata.

Groovy: When execution type is groovy, the application expects the condition expression to be a groovy script. The groovy script can be used to achieve many complicated calculations for determining a condition to be true or false.
When groovy script is given for filter expression, the application expects the groovy script in filter to return a string that will be applied to the report created using the metadata.

Step 8: Write the condition for permission (grant or deny) in the condition box.
For example, to restrict table/view/column from a user named “Mike”
$user.name eq ‘Mike’
Step 9: Filter expression can be applied when a particular data is to be filtered out from the condition applied.
For example, if user Mike from the above example is to be exempted from showing data of a client named ‘ABC Ltd’, filter expression can be written as:
meeting_details.client_name=’ABC Ltd’
And the condition would be:
$user.name eq ‘Mike’
To see Use case of Data Security, Click Here
Click here to view Several Use Cases
For More Info, Contact us at support@helicalinsight.com
